Thursday 12 May 2022, by Jérémy De Cock Tech
Today is a great day. We celebrate the release of our first tool available on Github. And it’s open source! This tool (more precisely a powershell script) helps to find evidences of compromission on a Windows workstation or server. The purpose?
On a Windows machine, we can find the registry which is nothing more than a large database used by the operating system. It contains the configuration data of the operating system and other installed software that want to use it.
An attacker, when he breaks into a computer, will from time to time modify this registry. It’ll help him to configure his own tools: hide a drive, retrieve information about the target’s system, start a program automatically when the machine starts, etc. So, he has to create registry keys. These keys, for us, are what we call artefacts that inform us about the presence of the attacker on the machine.
These are the evidences we are looking for!
How does the script work?
Our tool works with a dictionary: the user prepares beforehand his own lists (some of which are present on our GitHub) and then the script analyzes the registry and detects the presence of possible malicious keys.
Note: a list can match with a malware, a ransomware, an exploit, etc.
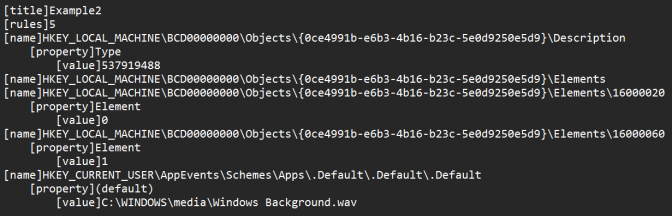
The tool searches on two drivers:
Once the analysis is completed, a report is generated allowing the user of the script to have an account of the vulnerabilities found (or not?) and to submit a score / list at the same time.
If you want to see an example of how to use the tool, we encourage you to check it out on our Github.